
At Black Hat and Def Con earlier this month, the penetration testing tool makers at Pwnie Express unveiled two new products aimed at extending the company's reach into the world of continuous enterprise security auditing. One, the Pwn Pro, is essentially a souped-up version of Pwnie Express' Pwn Plug line of devices; the other, Pwn Pulse, is a cloud-based software-as-a-service product that provides central control of a fleet of Pwn Pro “sensors.” Combined, the two are a whitehat’s personal NSA—intended to discover potential security problems introduced into enterprise networks before someone with malevolent intent does.
While Ars was given a brief look at the new products in Las Vegas, we’ll be conducting a more intensive, full review of Pwn Pro and Pwn Pulse in the near future. Rest assured that our review will be heavily informed by our experience with the Pwn Plug 2. But despite our somewhat brief experience with the new products, it’s not a stretch to say that they are a significant upgrade to Pwnie’s previous capabilities.First, some full disclosure: Ars has worked in the past with Pwnie Express Chief Technology Officer Dave Porcello. Specifically, Porcello helped us turn a Pwn Plug R2 into a miniature deep packet inspection machine during our collaboration with NPR. After that experience, we purchased a Pwn Plug R2 of our own to continue to perform vulnerability testing in our own lab. That means we have more than a passing familiarity with the team behind the Pwn products, but it also means we’ve put some mileage on the technology that underlies them as well.
Pwning like a pro
Pwnie Express’ Pwn Pro is a beefed-up version of the Pwn Plug R2, with a beefed-up price tag as well. Like the other Pwnie Express devices, the $1,995 Pwn Pro runs Pwnix, a custom distribution of Debian Linux derived from Offensive Security’s Kali Linux. Packaged with Pwnix are a collection of open source tools and custom code that allows a penetration tester or an organization’s security team to look for vulnerable devices and applications within a work environment—including rogue Wi-Fi hotspots, unsecured Bluetooth interfaces, and poorly secured network applications.
The Pwn Pro, like the Plugs before it, has a simple Web interface for overall configuration and control of its two “one-click” security-testing tools:
- Evil AP, a Wi-Fi attack tool that will automatically respond to the polling requests of wireless devices as networks they know, causing misconfigured devices to automatically connect to the Pwn Pro as a Wi-Fi hotspot.
- Passive Recon, a tool that listens to network traffic and performs an audit of connected devices, identifying their operating systems and software, as well as capturing cookies, passwords, and other data from unencrypted Web requests and other network traffic.
Others, such as the Metasploit penetration testing framework from Rapid7 and the 100 or so other tools in Pwnix’ s bag of tricks, can be launched via an SSH session. The box can find ways to phone home to a tester outside the network being monitored via one of six different covert channels configured in the product or via the included 4G/GSM USB modem included in the kit.
All of that is pretty familiar ground, essentially the same capabilities provided by the Pwn Plug R2 one year ago. But there are reasons that the Pwn Pro costs twice as much as last year’s model: it has improved computing power, a more purpose-built hardware platform, more out-of-the box features, and support for centralized management of multiple Pwn Pro devices through Pwn Pulse.
The Pwn Pro is a much more powerful device than its predecessors, based on an Intel Next Unit of Computing (NUC) architecture and built by a custom hardware manufacturer based in the US. With a 64-bit 1.8GHz Intel i3-3217U processor, 4GB of DDR3 memory, and 32GB of mSATA SSD storage, the Pwn Pro is a respectable step up from the Armada ARM-based Pwn Plug R2. The Pro’s design also has better provisions for keeping the fanless box cool.
Hopefully, the new hardware provider also means a boost in reliability—the first Pwn Plug R2 we purchased had a heat-related failure within a day. The Pwnie team eventually acknowledged that there was a string of such problems with the hardware manufacturer they contracted for the Pwn Plug R2.Since it’s slightly larger than the R2, the Pwn Pro also has room to consolidate its sensors inside the box. Like its predecessor, the Pro has a gigabit Ethernet adapter and built-in wireless networking: high-gain dual-band Wi-Fi supporting 802.11 a, b, g, and n networking. The Wi-Fi adapter can be used to turn the Pro into a hostile wireless access point, to launch packet-injection attacks against other networks, or simply to monitor wireless traffic. But unlike the Pwn Plug R2, the Pro has an internal Bluetooth radio, making it much easier (and less conspicuous) to deploy. To the untrained eye, the system just looks like a base station with two antennas. The broadband modem still uses an external USB connection.
In addition to the tools previously provided in Pwnix, the Pro includes a vulnerability scanner pre-loaded with a set of common exploit signatures. The scanner is compatible with Nessus’ vulnerability scan server as well, allowing for vulnerability scans to be automated and integrated with organizations’ security management workflow.
One cloud to rule them all
But perhaps the most powerful new feature of the Pwn Pro is its ability to integrate with Pwn Pulse, a new cloud-based service that makes it possible to centrally manage and monitor multiple Pwn Pro devices at multiple sites. In the Pulse Sensor configuration, the Pwn Pro is preconfigured to communicate securely with the Pulse cloud service (which runs on Amazon Web Services). Pwn Pulse is currently in beta testing.
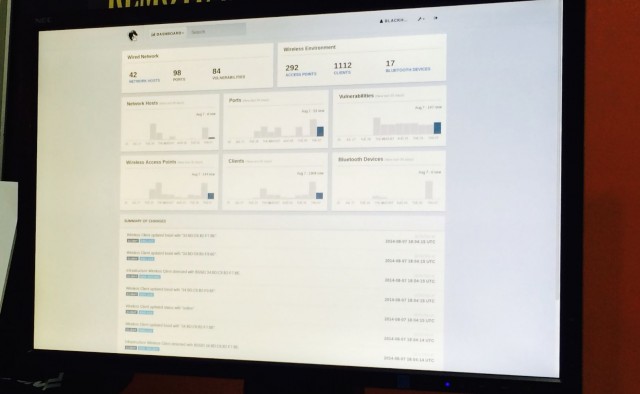
Pulse offers real-time monitoring of data from Pro sensors both individually and in aggregate. The service includes visualization tools providing an ongoing view of the security picture across an organization.
In addition to its “dashboard” view of incoming data, Pwn Pulse also lets an operator deploy custom scripts to run on remote Pro devices. This gives an organization’s security team a more scalable way to run a wide-ranging test against geographically dispersed networks rather than having to connect individually by SSH to each device.
We've been happy with our limited experience with Pwn Pulse. As soon as we acquire a Pwn Pro or two of our own, expect a more thorough test drive.
reader comments
18